CAS installation and configuration |
iServer, iPortal and iEdge supports CAS-based single sign-on (SSO). CAS (Central Authentication Service) is a Java open source project introduced by Yale University to build Web SSO. When you configure SSO, you need to setup a CAS authentication server. The CAS authentication server is responsible for the identification of user information. It can be deployed in a network environment. For details about CAS SSO configuration, see Configure to use CAS SSO.
You need to set up the CAS service to use CAS SSO. Below is the configuration method of CAS 3.X and CAS 5.X.
The CAS service is built by cas-server-webapp-3.4.war on the Windows system and MySQL is used as a database for storing user information.
From http://www.apereo.org, download the installation package for CAS 3.4, then extract cas-server-webapp-3.4.war, rename the extracted folder to cas, and add the following jar package to cas\WEB-INF\lib to connect to the user account’s database:
In addition, you need to download cas-server-3.4-release.zip and add all the jar packages in the modules folder of this zip package to the cas\WEB-INF\lib folder (except cas-server-core-3.4 .jar, as it is already included in cas-server-webapp-3.4).
Modify cas\WEB-INF\deployerConfigContext.xml to add the following configuration:
<bean id="dataSource" class="org.springframework.jdbc.datasource.DriverManagerDataSource">
<!--Based on the type of database-->
<property name="driverClassName" value="com.mysql.jdbc.Driver" />
<!--Database connection method-->
<property name="url" value="jdbc:mysql://localhost:3306/iportalusers" />
<!--Username and password for the local MySQL database-->
<property name="username" value="root" />
<property name="password" value="root" />
</bean>
Comment out the following line of code:
<!-- <bean class="org.jasig.cas.authentication.handler.support.SimpleTestUsernamePasswordAuthenticationHandler" /> -->
Under the <property name="authenticationHandlers"> node, find the subnode <list>, and add the following:
<bean class="org.jasig.cas.authentication.handler.support.HttpBasedServiceCredentialsAuthenticationHandler" p:httpClient-ref="httpClient" />
<bean class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler">
<property name="dataSource" ref="dataSource" />
<property name="sql" value="select password from users where lower(user ) = lower(?)" />
</bean>
The bold fields in the above code represent:
Note: If you are using a cas server - webapp - 3.5.2 version, still need in cas\WEB - INF\deployerConfigContext XML file, Find < bean class = "org. Jasig. Cas. Services. RegexRegisteredService" > nodes, increase under the node allowedAttributes properties, add content is as follows:
...
<property name="allowedAttributes">
<list>
<value>roletype</value>
<value>guid</value>
</list>
</property>
...
The meaning of the bold fields in the above code is as follows:
Modify cas\WEB-INF\deployerConfigContext.xml,and write down the following lines of code:
<!-- <bean id="attributeRepository" class="org.jasig.services.persondir.support.StubPersonAttributeDao">
<property name="backingMap">
<map>
<entry key="uid" value="uid" />
<entry key="eduPersonAffiliation" value="eduPersonAffiliation" />
<entry key="groupMembership" value="groupMembership" />
</map>
</property>
</bean> -->
Add the following configuration:
<bean class="org.jasig.services.persondir.support.jdbc.SingleRowJdbcPersonAttributeDao" id="attributeRepository">
<!-- Specify the data source to use, here dataSource is a configured data source -->
<constructor-arg index="0" ref="dataSource"/>
<!-- SQL statement for querying information from the database, users is the table name of the user account -->
<constructor-arg index="1" value="select * from users where {0}"/>
<property name="queryAttributeMapping">
<map>
<!-- user is the name field of the account table -->
<entry key="username" value="user "/>
</map>
</property>
<property name="resultAttributeMapping">
<map>
<!—Configure the returned field information: usertype is the type of the account, id is the id of the account, and roletype is used for the iPortal configuration, that is, the CAS user attribute field. -->
<entry key="usertype " value="roletype "/>
<entry key="id" value="guid"/>
</map>
</property>
</bean>
The bold fields in the above code represent:
Find the "bean" whoes class is " org.jasig.cas.authentication.AuthenticationManagerImpl" of bean, find the <list> node of the <property name="credentialsToPrincipalResolvers"> node, modify the following content of the <list>node:
<bean class="org.jasig.cas.authentication.principal.UsernamePasswordCredentialsToPrincipalResolver" />
to:
<bean class="org.jasig.cas.authentication.principal.UsernamePasswordCredentialsToPrincipalResolver" >
<property name="attributeRepository" ref="attributeRepository" />
</bean>
For returning the attribute information, you also need to modifiy the WEB-INF\view\jsp\protocol\2.0\casServiceValidationSuccess.jsp file in the CAS directory. The specific method is: at the end of the <cas:user>${fn:escapeXml(assertion.chainedAuthentications[fn:length(assertion.chainedAuthentications)-1].principal.id)}</cas:user>, add:
<cas:attributes>
<cas:test>test_value</cas:test>
<c:forEach var="auth" items="${assertion.chainedAuthentications}">
<c:forEach var="attr" items="${auth.principal.attributes}">
<cas:${fn:escapeXml(attr.key)}>${fn:escapeXml(attr.value)}</cas:${fn:escapeXml(attr.key)}>
</c:forEach>
</c:forEach>
</cas:attributes>
Modify cas\WEB-INF\spring-configuration\ticketGrantingTicketCookieGenerator.xml file to allow users to log in the CAS by using the http protocol. The method is: set the "p:cookieSecure" of the "CookieRetrievingCookieGenerator" as "false".
After the configuration, place the CAS folder in the webapps directory of Tomcat and start the Tomcat. At this stage, you can access http://casserver:port/cas and log in to the CAS with the accounts in the users table of the iportalusers database configured above.
iServer/iPortal/iEdge supports CAS 5.x SSO since the 9D released. CAS 5.x requires a Java8 environment. While the CAS 5.x is significantly different with CAS 3.x, and the deployment is different too, and there is no official 5.x released version. So users need to manually build the war package. There are two common ways to build a server for CAS:
Based on source code
Install using WAR Overlay
The recommendation is to use the second one, which is easy to configure and manage, and subsequent upgrades are also easy. Therefore, the Windows system is taken as an example to introduce the specific steps of building a service using WAR Overlay.
Since there is no release version of CAS 5.X, you need to use Git to download CAS Overlay. After switching to the download directory, enter the following git command to download:
git clone -b 5.3 https://github.com/apereo/cas-overlay-template.git
After the download is complete, a new folder called "cas-overlay-template" is added to the directory.
Create database, table and account data in the database for CAS to manage iServer/iPortal/iEdge account information. Here is an example of a MySQL database:
CREATE DATABASE `localmysql`;
DROP TABLE IF EXISTS `app_user`;
CREATE TABLE `app_user` (
`id` INT(11) NOT NULL AUTO_INCREMENT,
`username` VARCHAR(45) DEFAULT NULL,
`password` VARCHAR(45) DEFAULT NULL,
`role` VARCHAR(45) DEFAULT NULL,
PRIMARY KEY (`id`)
);
INSERT INTO `app_user` VALUES (1,'cas','1234567','admin');
To implement the SSO with iServer/Portal/iEdge, you need to find the pom.xml file in the cas-overlay-template directory, add the following dependencies.
To add JDBC plugins to the database, add the following dependencies to pom.xml:
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-jdbc</artifactId>
<version>${cas.version}</version>
</dependency>
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-jdbc-drivers</artifactId>
<version>${cas.version}</version>
</dependency>
The ticket verification between iServer/Portal/iEdge and CAS follow the SAML1.1 protocol, so the CAS needs to include the following dependencies to enable support for SAML1.1:
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-saml</artifactId>
<version>${cas.version}</version>
</dependency>
CAS registers services in JSON format, so you need to include JSON dependencies to support JSON, as follows:
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-json-service-registry</artifactId>
<version>${cas.version}</version>
</dependency>
When implementing the ticket verification response between iServer/Portal/iEdge and CAS, you need to get the field that represents the role (that is, the role field in the previous table) to verify the type of permission. So you need to add the attribute returning dependency package.
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-core-authentication-attributes</artifactId>
<version>${cas.version}</version>
</dependency>
At this point, all the dependencies needed for the iServer/iPortal/iEdge docking CAS have already been added. Use the following command to package:
mvn package
After the packaging is complete, copy the generated CAS.war into the webapps directory of Tomcat.
Modify the configuration file, but note that Tomcat cannot be started at this time.
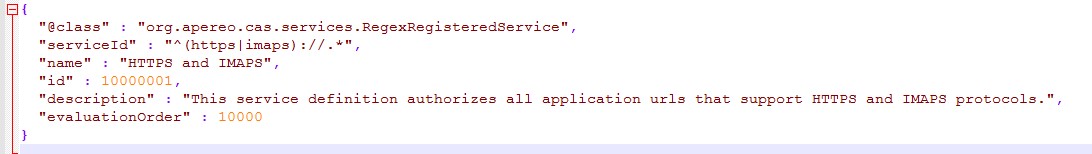
First open the catalog HTTPSandIMAPS-10000001.json file under cas \WEB-INF\classes\services directory, shown as follows:

According to the serviceId parameter, the current CAS only supports two protocols: https and imaps. We still need to add the http protocol as follows:
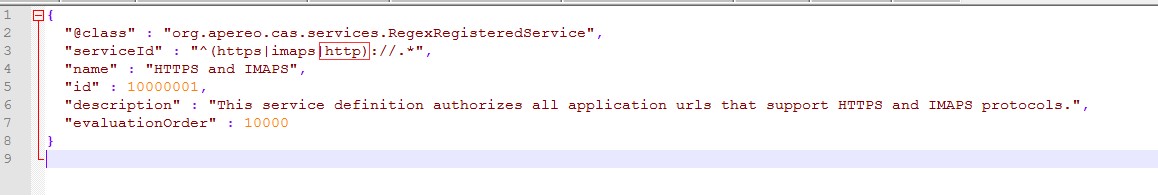
Add the configuration for registering services as follows:
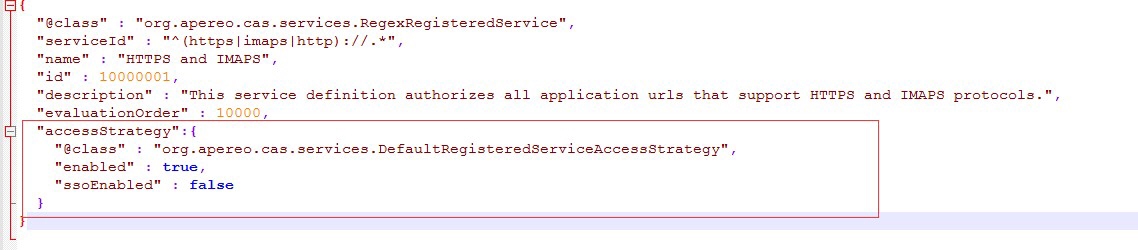
Add the configuration that returns all related properties as follows:
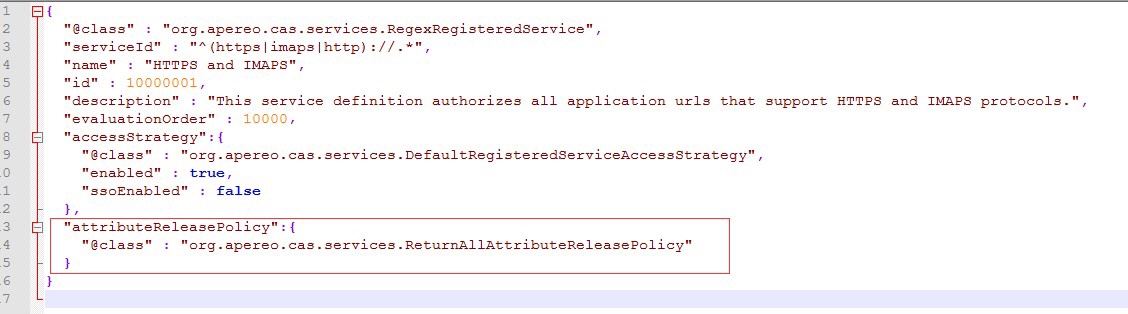
Save the HTTPSandIMAPS-10000001.json file. Then open the Apereo-10000002.json file shown as below:
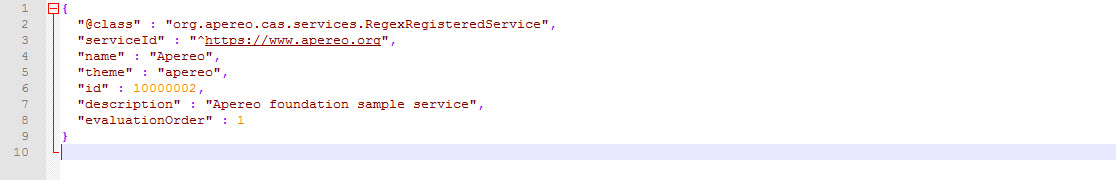
Referring to the HTTPSandIMAPS-10000001.json file, make the same modifications to the serviceId parameter as follows:
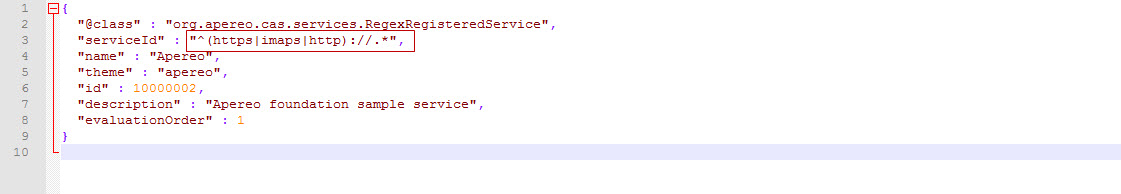
At this point, the modification of the configuration file is completed.
In the cas\WEB-INF\classes directory create a new application.properties file, add the following configuration item to open the service registry from json:
#Enable the service registry from json
cas.serviceRegistry.initFromJson=true
Add the following configuration item to set the service registration configuration file location:
#Set the service registration configuration file location
cas.serviceRegistry.json.location=classpath:/services
Add database configuration items for logging in to the CAS server (if not configured, there will be no way to login to the CAS server using the username and password in MySQL); where localmysql is the database name you created in the previous step, and app_user is the created table. See the details as follows:
# JDBC configuration
# Database connection
cas.authn.jdbc.query[0].url=jdbc:mysql://localhost:3306/localmysql?useUnicode=true&characterEncoding=UTF-8&autoReconnect=true&useSSL=false&serverTimezone=UTC
# The dialect configuration for database
cas.authn.jdbc.query[0].dialect=org.hibernate.dialect.MySQLDialect
# User name of the database
cas.authn.jdbc.query[0].user=root
# Password of the user
cas.authn.jdbc.query[0].password=123456
# Whether to enable the auto commit function for the database transactions
cas.authn.jdbc.query[0].autocommit=false
# Database driver
cas.authn.jdbc.query[0].driverClass=com.mysql.jdbc.Driver
# Set the time out
cas.authn.jdbc.query[0].idleTimeout=5000
# The sql for querying the password of the account. Requires to contain the password field.
cas.authn.jdbc.query[0].sql=select * from app_user where username=?
# Specify the queried fields of the above sql statement. (Required)
cas.authn.jdbc.query[0].fieldPassword=password
Enable the singleRow attribute configuration to allow returning fields to the client when the CAS server performs the authentication. If not configured, other fields in the data table, such as the role field in the previous table, cannot be obtained. The configuration is as follows:
# singleRow attribute
# Enable singleRow attribute
cas.authn.attributeRepository.jdbc[0].singleRow=true
# Set the mapping relationship between the database table and the cas server query results.
cas.authn.attributeRepository.jdbc[0].attributes.username=username
cas.authn.attributeRepository.jdbc[0].attributes.password=password
cas.authn.attributeRepository.jdbc[0].attributes.role=role
cas.authn.attributeRepository.jdbc[0].order=0
# Return all the attributes.
cas.authn.attributeRepository.jdbc[0].requireAllAttributes=true
# Query all the attribute fields.
cas.authn.attributeRepository.jdbc[0].sql=SELECT * FROM app_user WHERE {0}
# Specify the query condition in the above sql statement.
cas.authn.attributeRepository.jdbc[0].username=username
Note:
a. The cas.authn.attributeRepository.jdbc[0].attributes parameter is only the mapping relationship of the query results. The structure of the table is subject to the practice table structure. The results of the table here are the username, password, and role fields.
b. The cas.authn.attributeRepository.jdbc[0].sql parameter is just a SQL statement used by CAS to query the database. It is very liberal and it is possible to use other correct query statements. For example, when storing data in the form of two associated tables in the database, the SQL statement can be written as:
SELECT app_user.*,gl1.* FROM app_user,gl1 WHERE app_user.test = gl1.test and {0}
Among them, the app_user table and the gl1 table are associated by the test field.
The complete application.properties is as follows:
#Open json registration service
cas.serviceRegistry.initFromJson=true
#Set the service registration profile location
cas.serviceRegistry.json.location=classpath:/services
# JDBC configuration
#Database connection
cas.authn.jdbc.query[0].url=jdbc:mysql://localhost:3306/localmysql?useUnicode=true&characterEncoding=UTF-8&autoReconnect=true&useSSL=false&serverTimezone=UTC
#Database dialect configuration
cas.authn.jdbc.query[0].dialect=org.hibernate.dialect.MySQLDialect
#Database username
cas.authn.jdbc.query[0].user=root
#Database user password
cas.authn.jdbc.query[0].password=123456
#Database transaction auto-commit
cas.authn.jdbc.query[0].autocommit=false
#Database driver
cas.authn.jdbc.query[0].driverClass=com.mysql.jdbc.Driver
#Timeout configuration
cas.authn.jdbc.query[0].idleTimeout=5000
#The SQL for querying account password, must contain password field
cas.authn.jdbc.query[0].sql=select * from app_user where username=?
#Specify the above SQL query field name (required)
cas.authn.jdbc.query[0].fieldPassword=password
#Single row attribute
#Open single-line attributes
cas.authn.attributeRepository.jdbc[0].singleRow=true
#Set the mapping relationship between database tables and CAS server query results. Specifically, the attributes should be consistent with the fields of the actual database.
cas.authn.attributeRepository.jdbc[0].attributes.username=username
cas.authn.attributeRepository.jdbc[0].attributes.password=password
cas.authn.attributeRepository.jdbc[0].attributes.role=role
cas.authn.attributeRepository.jdbc[0].order=0
#Return all attributes
cas.authn.attributeRepository.jdbc[0].requireAllAttributes=true
#The SQL statement for querying all the attribute fields
cas.authn.attributeRepository.jdbc[0].sql=SELECT * FROM app_user WHERE {0}
#Specify the above SQL query conditions
cas.authn.attributeRepository.jdbc[0].username=username
#Database connection
cas.authn.attributeRepository.jdbc[0].url=jdbc:mysql://localhost:3306/localmysql?useUnicode=true&characterEncoding=UTF-8&autoReconnect=true&useSSL=false&serverTimezone=UTC
#Database dialect configuration
cas.authn.attributeRepository.jdbc[0].dialect=org.hibernate.dialect.MySQLDialect
#Database username
cas.authn.attributeRepository.jdbc[0].user=root
#Database user password
cas.authn.attributeRepository.jdbc[0].password=123456
#Database transaction auto-commit
cas.authn.attributeRepository.jdbc[0].autocommit=false
#Database driver
cas.authn.attributeRepository.jdbc[0].driverClass=com.mysql.jdbc.Driver
#Timeout configuration
cas.authn.attributeRepository.jdbc[0].idleTimeout=5000
At this point, the configuration of CAS 5.X is completed.